Hacked WordPress sites can be a nightmare for any website owner. Data can be lost, security can be compromised, and reputation can be damaged. If your WordPress site is hacked, don’t panic. In this guide, we will walk you through the crucial steps of recovering from a hacked website and preventing future attacks.
Signs That Your WordPress Site Has Been Hacked
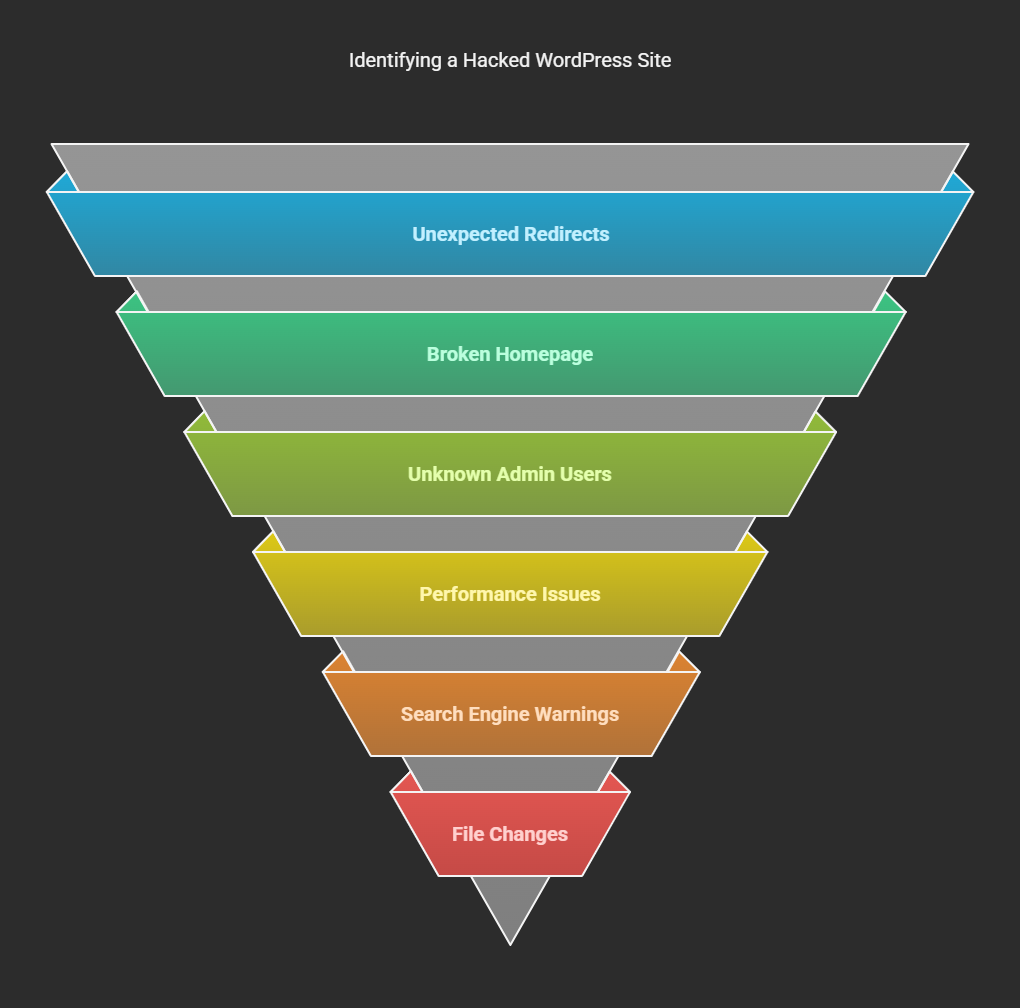
First, established steps should be taken to investigate if the site indeed succumbed to hacking. Some signs could include:
➤Unexpected redirects – The site redirects to some malicious or unknown websites.
➤Broken homepage – Your home page is modified or taken over by a message from a hacker.
➤Unknown admin user – Unknown users within the roles of administrator have appeared in your WordPress dashboard.
➤A slow or crashing website – Your site frequently becomes slow in loading. It usually crashes due to excessive usage of resources.
➤Warnings from search engines – Google or other engines inform you of a compromise in your site.
➤Suspicious change of files– Some are unknown files or changes in your core WordPress files.
➤Disabling security plugins – Security plugins like Wordfence or Sucuri are disabled without your authority.
If you see any of these signals, then there is a possibility that your WordPress site has been hacked and immediate actions need to take.
Step-by-Step Guide to Fix a Hacked WordPress Site
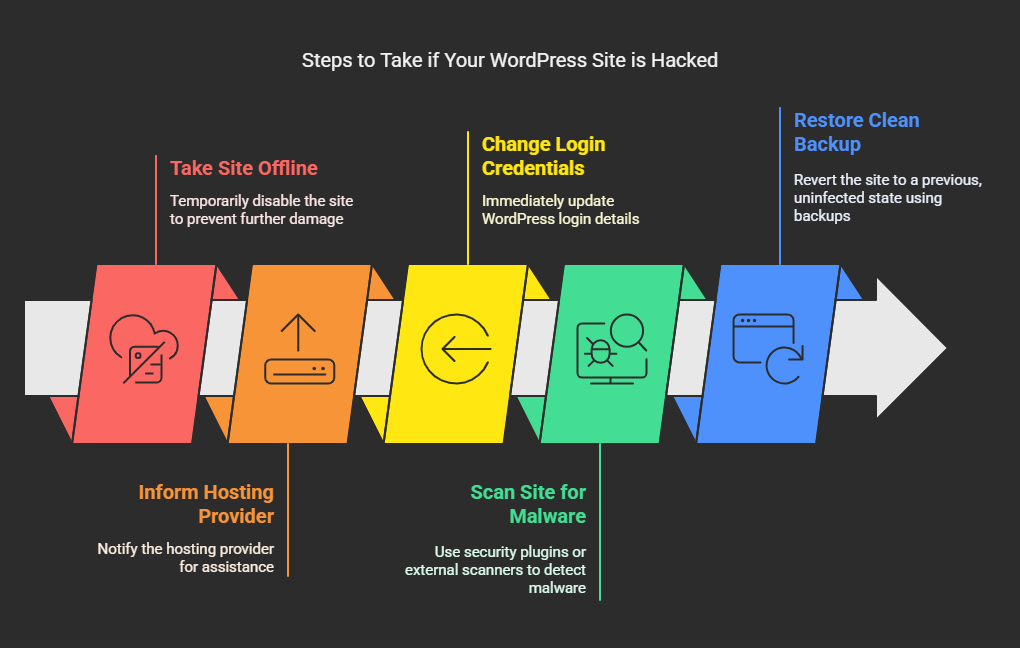
1. Take a Deep Breath and Take Your Site Offline
If you think your site is hacked, the first action to take is to prevent further damage:
➤Temporarily take your site offline making use of a maintenance mode plugin.
➤Inform your hosting provider about the issue; they might help scanning and restoring backups.
➤Immediately change your WordPress log-in credentials.
2. Virus Scan Your Site
Use Wordfence, Sucuri, or MalCare as a WordPress security plugin to scan your site for malware. If you do not have access to the dashboard, an external scanner such as Google Safe Browsing or Sucuri SiteCheck should be used to detect malware.
3. Restore a Clean Backup
For instance, if you have a clean backup available, you can restore your website to a previous date. This can be done through:
➤Your hosting provider’s backup system.
➤Using a plugin like UpdraftPlus or BackupBuddy.
➤Long-term manual backup for local files.
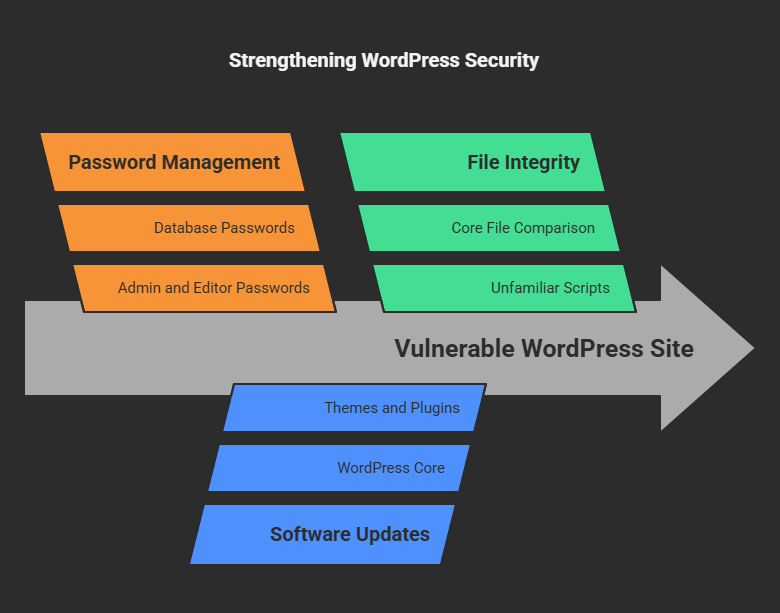
4. Change All Passwords and User Credentials
This means that all passwords must be changed for all:
➤WordPress admin, editor, and contributor accounts.
➤Hosting account, such as those for cPanel, Plesk, or DirectAdmin.
➤FTP/SFTP accounts.
➤Database (update wp-config.php with the new database password).
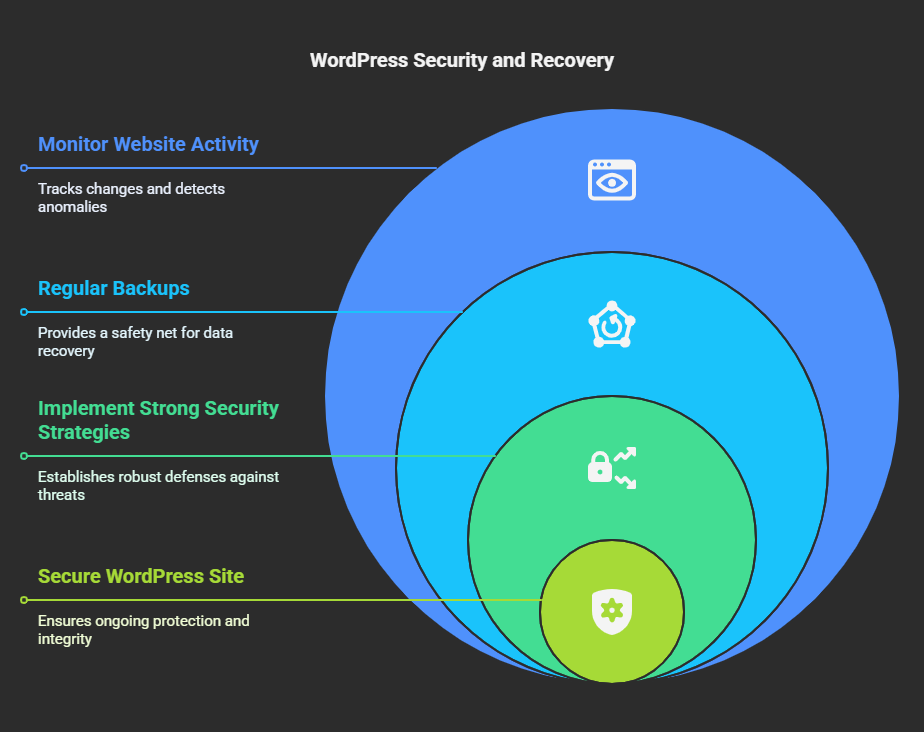
Once clear, you can keep using uniquely strong passwords and Two-Factor Authentication (2FA) for superior security.
5. Update your WordPress, Themes, and Plugins
Old software exploits hacked sites. Upgrade:
➤To the latest version of WordPress core.
➤All installed themes and plugins.
➤Your version of PHP (via the controls provided through your hosting provider).
If the plugin or theme has not been upgraded for quite a long period by its developer, think of removing it and replace it with another more secure variant.
6.Check and Clean Core WordPress Files:
Malicious hackers usually access core files of WordPress and modify them. You need to compare your files with a fresh installation to find the difference.
➤Download a new copy of WordPress directly from WordPress.org.
➤Then upload compromised files like wp-config.php, .htaccess, and index.php.
➤Delete files or scripts that you’re not familiar with in the wp-content/uploads directory.
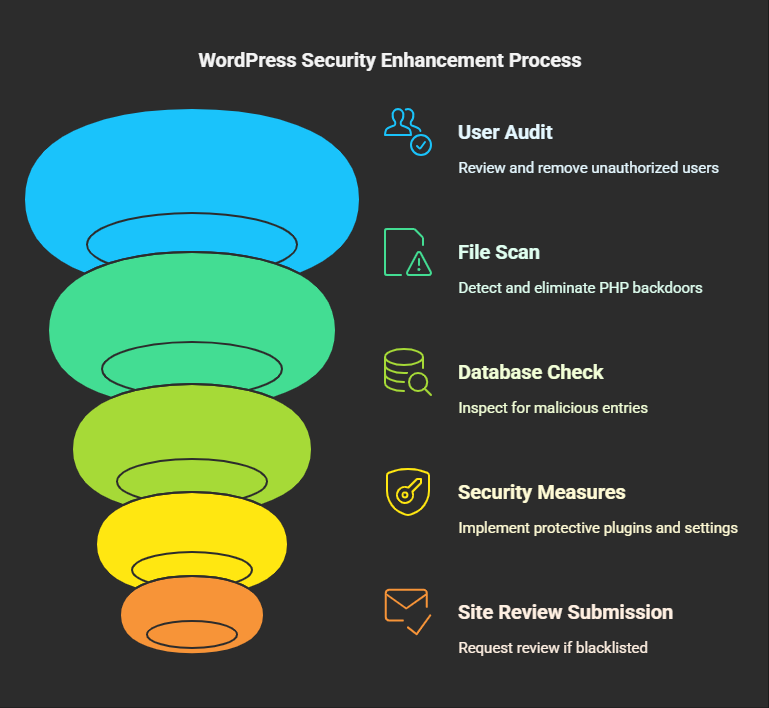
7. Get Rid of Suspicious Users and Backdoors.
➤Check Users under WordPress Admin and delete any unauthorized users.
➤Scan for PHP backdoors in the theme or plugin files or the wp-content/uploads directory.
➤Scan for suspicious-looking code with the help of a plugin such as Exploit Scanner.
8. Check and Secure Database
Hackers may inject malicious code into your database.
➤Use phpMyAdmin to check the wp_users and wp_options tables for unknown users or settings.
➤Run an SQL query to find suspicious entries:
SELECT * FROM wp_users;
SELECT * FROM wp_options WHERE option_name LIKE '%admin%';➤Remove any unknown database entries.
9. Implement a Strong Security Strategy
Now that your site is clean, implement the following security measures:
➤Set Security Plugin: Wordfence or Sucuri or iThemes Security basically services to check on-nearing threats.
➤Web Application Firewall (Waf): Services like cloudflare or sucurifirewall are now used for attacking malicious traffic.
➤Disable File Editing: As protection from code tampering, use this in file wp-config.php
define('DISALLOW_FILE_EDIT', true);➤Restrict Login Attempts: Limit failed login attempts by plugin such as Limit Login Attempts Reloaded.
➤Change Default Login URL: Use a plugin like WPS Hide Login to modify wp-admin to a specific URL.
10. Submission for Site Review (If Blacklisted)
Request a review if your site is blacklisted by Google or marked as unsafe.
➤Use Google Search Console to check for security issues and request a review.
➤If Sucuri is being used, read through their guide to request blacklist removal.
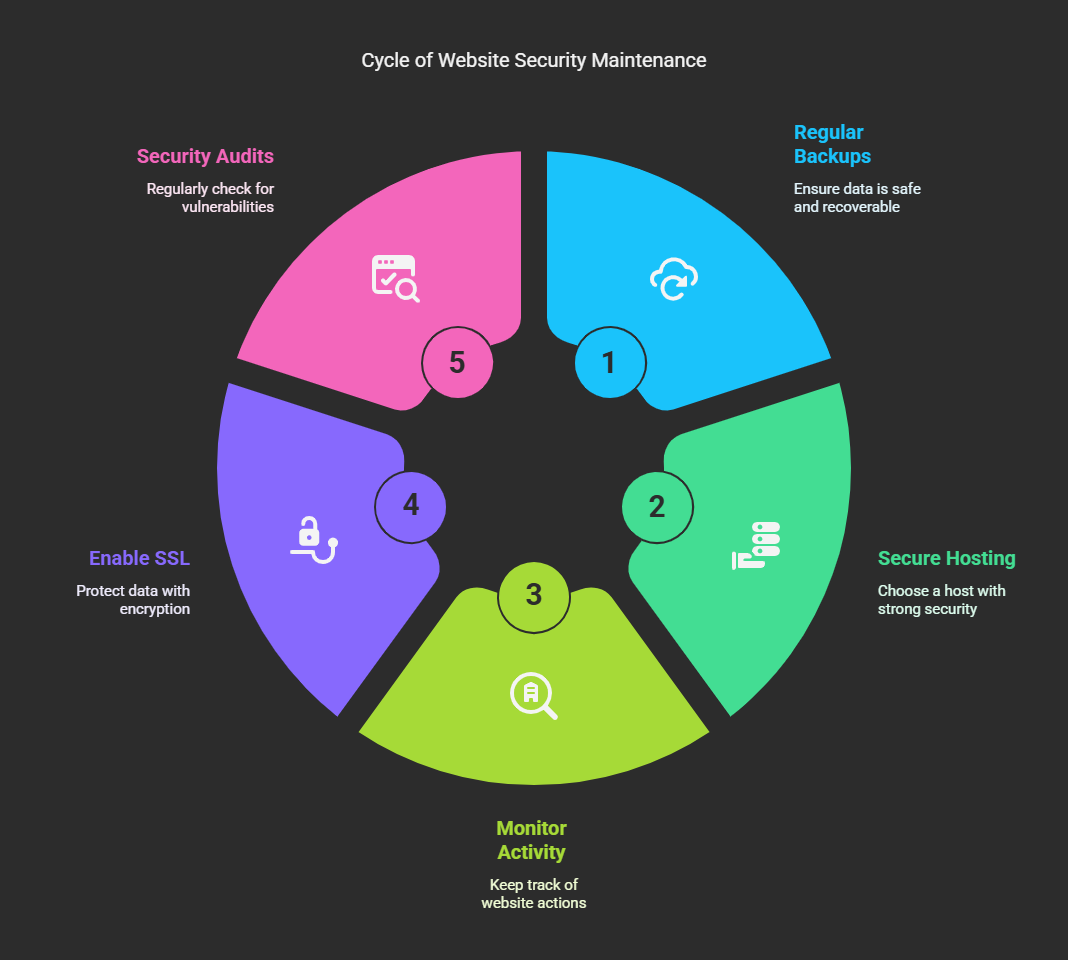
Preventing Future Hacks
After getting your site secure, there are other steps you can take to prevent attacks in the future:
➤Regular Backups: set up automatic backups with UpdraftPlus or VaultPress.
➤Use a Secure Hosting Provider: Find a host with top-notch security such as SiteGround, Kinsta, or WP Engine.
➤Monitor Website Activity: Install WP Activity Log and monitor activities on the docket.
➤Enable SSL Certificate: Secure your site with HTTPS to encrypt the exchange of data.
➤Conduct Regular Security Audits: Scan your site weekly for malware and vulnerabilities.
Conclusion
You will get updates on data until October 2023. Restoring a hacked WordPress site can be challenging. But if the right approaches are taken, you can fix your websites and save them from future attacks. Security measures should be implemented to its fullest, WordPress applications kept up-to-date, and threats watched for regularly to keep hackers at bay from your website while ensuring pleasant use by your visitors.